FЯIDA - Method hooking
FЯIDA - Method hooking
We saw how we used the universal ssl pinning bypass script to bypass ssl pinning. We will now make our own custom script to hook a method and change it’s function in runtime to bypass root detection. We will use androgoat apk.
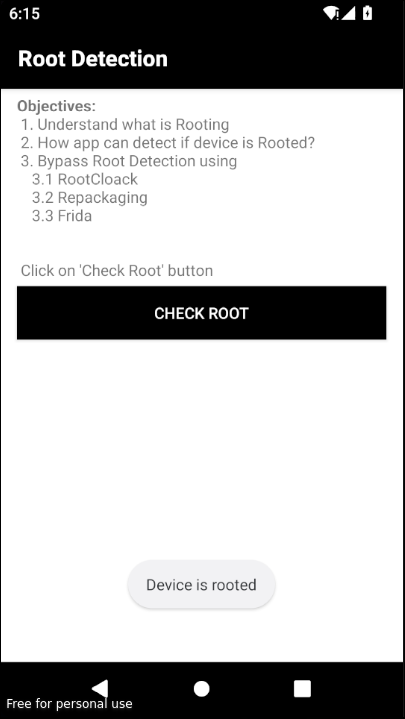
From the reverse engineering blog we saw the isRooted() function that checks whether the device is rooted.
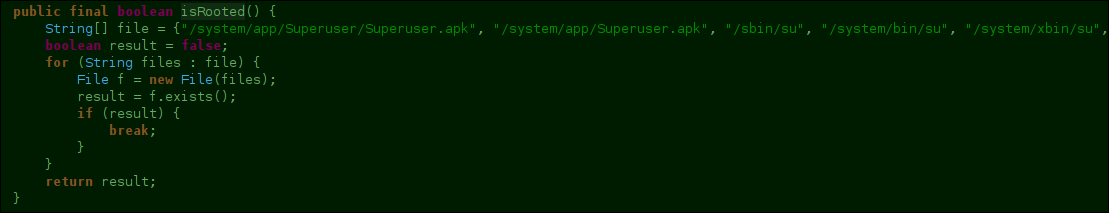
We will now change the function return type to always be false using this custom script.
Java.perform(function () {
// we create a javascript wrapper for RootDetectionActivity
var RootDetectionActivity = Java.use('owasp.sat.agoat.RootDetectionActivity');
// implement our function
RootDetectionActivity.isRooted.implementation = function () {
// console.log is used to report information back to us
console.log("Inside isRooted() function...");
// return false
return false
};
});
Let’s run frida. Make sure you always run the server first before running the scripts to avoid getting errors.
frida -l custom_root_bypass.js -f owasp.sat.agoat -U
____
/ _ | Frida 16.1.4 - A world-class dynamic instrumentation toolkit
| (_| |
> _ | Commands:
/_/ |_| help -> Displays the help system
. . . . object? -> Display information about 'object'
. . . . exit/quit -> Exit
. . . .
. . . . More info at https://frida.re/docs/home/
. . . .
. . . . Connected to Nexus 5 (id=127.0.0.1:6555)
Spawned `owasp.sat.agoat`. Resuming main thread!
[Nexus 5::owasp.sat.agoat ]-> Inside isRooted() function...
Inside isRooted() function...
We were able to bypass the Root detection.
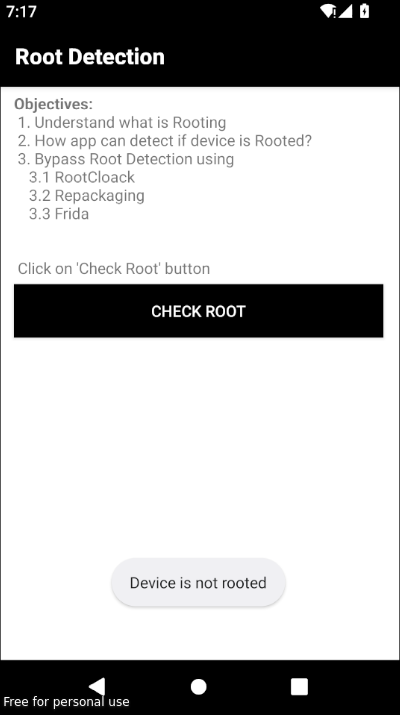
We can bypass any functions or manipulate them as long as we can reverse the apk and understand the functions and how they operate.
FRida scripts
Read other posts